
Today, there are many new tech ideas that might seem hard to understand. What is tokenization? It’s a new way to make payment card data safer and is also linked to something called blockchain, which is used for digital money like Bitcoin.
Even though a lot of people are talking about tokens, many still wonder what it is and how it works. If you’ve ever wondered about it, you’re in the right place!
Keep reading to find out what tokenization is, the different types, its good and bad sides, and how it might help your business work better.
- 1. What is Tokenization? Tokenization Meaning
- 2. How Does Tokenization Work? Tokenizer Algorithm Explained
- 3. Examples of Tokenization in Different Industries
- 4. What are the Different Types of Tokenization?
- 5. Advantages & Disadvantages of Tokenization
- 6. Tokenization vs. Encryption: What’s the Difference?
- 7. Steps Involved in the Tokenization Process
- 8. Challenges and Considerations when Implementing Tokenization
- 9. Future Trends and Advancements in Tokenization Technology
- 10. Key Takeaways
What is Tokenization? Tokenization Meaning

Digital tokenization is the process of breaking down a text document into smaller units called tokens. These tokens can be individual words, phrases, or even characters. It is a crucial step in natural language processing and helps to analyze and understand the text data more effectively.
Furthermore, if we dive deeper into the question “What is tokenization”, we usually hear the terms crypto token and NFT (non-fungible token). But it is also a way to protect sensitive cardholder data or represent digital assets, such as credit card processing and payment processing, in accordance with industry standards for data security and government regulations. In one sense, it’s about replacing important data, like credit card data, with a “token” that’s less valuable, such as a debit card. This helps keep data safe because even if someone gets the token, they can’t get the real data without the right system. Tokenization of data preserves credit card and bank account information in a virtualized vault, allowing enterprises to securely transmit critical information, such as financial transactions, via computer networks.
This system must be secured and validated using security best practices applicable to sensitive data protection, secure storage, audit, authentication, and authorization. When you process a payment using the token stored in your systems, only the original credit card tokenization system can swap the token with the corresponding primary account number (PAN) and send it to the payment processor for authorization. Your systems never record, transmit, or store the PAN, only the token. It helps companies achieve PCI DSS compliance by reducing the amount of PAN data and social security numbers stored in-house.
It can also be used in the world of digital currencies like Bitcoin. Here, real-world assets or value (like computer power) are turned into digital tokens on a blockchain. This makes them easy to track and use online.
What is tokenization with an example? When you pay with a credit card, the real card number might be hidden and replaced with a token. So, the seller doesn’t see the actual card number, just the token. This helps make payments safer in our digital world. This should also answer the tokenization meaning.
How Does Tokenization Work? Tokenizer Algorithm Explained
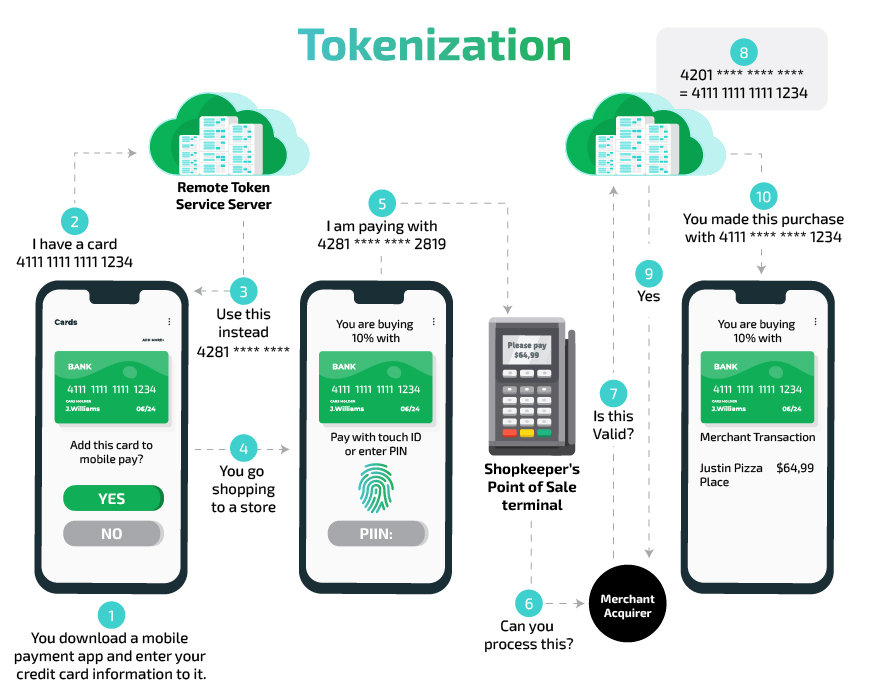
Share this Image on Your Site:
First, we’ve explained, “What is tokenization”. Now, how does tokenization work? Imagine you want to buy a toy online with a credit card. When you enter your card details, the website changes those details into a secret code called a “token.” This way, no one can see your real card information. The website’s payment system makes this token.
Next, this token is locked up with an extra layer of protection before it’s sent across the internet to the place that checks if your card can pay for the toy. The original card details are kept safe in special storage. Only this storage knows how to turn the token back into your real card information.
Lastly, the payment system protects the information even more before sending it to the bank to make sure the payment is okay. If everything looks good, a message saying the payment was successful is sent to everyone involved, like the website, the bank, and you.
Examples of Tokenization in Different Industries

Understanding what is tokenization, requires looking at examples in different industries. It’s like turning things into digital tokens or coins. Think about how people buy and sell land. Nowadays, land can be turned into digital tokens, known as blockchain tokens. This makes it easier for people to trade or sell land, including in the stock trading industry. Another example is when companies want to keep customer data safe. They turn this data into tokens too. In the physical world, coin tokens, such as casino tokens, have a long history of use replacing the financial instrument of minted coins and banknotes.
The concept of tokenization is commonly used in blockchain technology to secure the ownership of assets, protect data, participate in crypto investing, and assign the created token value to its original value. To enable permitted look-ups of the original value using the token as the index, a secure cross-reference database must be constructed. Basically, whenever there’s something we want to keep private or trade easily, we can use tokens to help with that.

Unlock Your Crypto Potential: Become a Market Maverick with Expert Coaching!
Are you ready to dive into cryptocurrency but need some advice? With our personalized 1:1 coaching, you’ll learn to:
Understand – the fundamentals of cryptos and how they impact value.
Navigate – through the volatile crypto market with confidence.
Identify – new lucrative opportunities that maximize returns.
Manage – exchanges and risk to protect your investments.
BOOK EXPERT COACHING NOWWhat are the Different Types of Tokenization?
What is tokenization should be clear now, but again, imagine you have a toy box, and in this toy box, you have all sorts of toys: action figures, toy cars, stuffed animals, and even some shiny gold coins. Each of these toys represents something different. In the world of cryptography and cryptocurrencies, these “toys” are called tokens, and they represent various things too!
Tokenization Outside of the Blockchain with Examples
First, let’s talk about the different types of tokenization outside of the decentralized blockchain and cryptocurrency world. You might find in this digital toy box:
1. Vaultless tokenization
Vaultless tokenization is a way to protect sensitive information, like your credit card number, by turning it into a random set of numbers and letters, called a token. This token is useless to anyone who might try to steal it because it doesn’t contain any of your real information. Imagine if your house key was turned into a different shape – even if someone else got it, they couldn’t use it to open your door. This keeps your actual information, like your real house key, safe and secure. Vaultless tokenization means there isn’t a central “vault” or storage place where all the sensitive information is kept, making it even harder for thieves to access.
With vaultless tokens, the sensitive information is stored using an algorithm, eliminating the need for a secure database. If the token is reversible, then the original information is generally not stored in a vault. This makes the sensitive information encrypted message unreadable to anyone without a key, even when they can see the encrypted message. It substitutes sensitive information with non-sensitive equivalents, referred to as tokens. This may utilize any of these processes: With a key, a theoretically reversible cryptographic function. A function that cannot be reversed, like a hash function. The replacement information is referred to as a token.
2. Vault Tokenization (Meet PCI DSS Requirements)
Vault is a type of tokenization that keeps your sensitive payment information, such as your credit card number, safe and secure at the point-of-sale (POS) system or online checkout form. When you buy something online, Vault replaces your real credit card number with this special code, which is known as a token. Only the Vault knows how to turn that code back into your real payment information. This way, your actual credit card number is kept secret and safe from hackers or other bad people who might want to steal it. It’s like having a secret language that only you and the token vault understand! To meet PCI DSS requirements is the main task for a card issuer.
3. NLP Tokenization
What is tokenization in NLP? In the world of Natural Language Processing (NLP), which is all about teaching computers to understand human language, it’s like breaking a chocolate bar into pieces.
When we talk or write, we use sentences made up of words. Tokenization is the process of taking a long sentence and breaking it up into smaller parts, usually words. For example, the sentence “I love chocolate” would be tokenized into three parts or “tokens”: “I”, “love”, and “chocolate”.
By doing this, it’s easier for computers to look at each word individually and understand the meaning or structure of a sentence. Just like it’s easier to share a chocolate bar when it’s broken into pieces!

Unlock the Code: Master Blockchain Programming!
Dive into the world of decentralized technology with our comprehensive online programming courses. Learn at your own pace and get:
Access – to expert instructors.
Interactive – coding exercises.
Vibrant – community of like-minded learners.
Certified – receive your recognized diploma.
ENROLL TODAY AND TRANSFORM YOUR FUTURE!Blockchain Tokenization Types with Examples
So what is tokenization on Blockchains? There are different types of tokens on the blockchain, each with its own purpose, like tickets for rides, stocks in a company, digital dollars, or online collectibles.
1. Utility Tokens
These are like the action figures in your toy box. You buy them not because they’re made of gold or are rare, but because they let you do something special. In the digital world, utility tokens give you access to specific features in a project. Think of it as a ticket to a special club or a key that unlocks a game level. Filecoin is a very good example of a utility token. Imagine you have extra space on your computer and you want to “rent” it out. Filecoin lets you do that. When people use your space, you get Filecoin tokens.
2. Security Tokens
Think of these as shiny gold coins. They represent ownership in something, like owning a part of a company or an asset. If the company does well, the value of your coin might go up, just like a rare gold coin might be worth more if people really want it. The best example of a security token is in Real Estate. By buying a token, you buy a piece of the property. This method allows more people to invest in real estate, even if they don’t have a lot of money, and it makes things easier and more flexible for everyone.
3. Stablecoins
Imagine a toy car in your box that always runs at the same speed, no matter what. Stablecoins are like that. Their value is tied to something stable, like the dollar. This means that even if other things in the crypto world are going up and down in value, stablecoins try to stay the same. Tehters’ USDT is a great example of a stablecoin.
4. Non-Fungible Tokens (NFTs)
These are like your unique, one-of-a-kind stuffed animals. No two are exactly the same. NFTs are digital tokens that represent unique items or pieces of content. Think of them as collectible digital art, where each piece is special and different from the rest. the highest-paid NFT was a digital artwork titled “Everydays: The First 5000 Days” by the artist Beeple, which sold for $69.3 million at a Christie‘s auction in March 2021.
5. Governance Tokens
Imagine you have a small toy council where toy representatives make decisions about the toy box’s rules. If you have a governance token, it’s like being part of that council. It lets you have a say in how a crypto project is run.
So, in our digital toy box, we have different tokens that all serve unique purposes, just like the toys you might have in a real toy box at home! A good example of a governance token is the “Maker (MKR)” token associated with the MakerDAO platform.
Other Types of Tokens
You often hear about ICO or Cryptocurrency tokenization. Well, these are special types and mostly they belong to the category of Security or Utility Token. It depends on whether you receive company shares or the right to use a network. The same applies to the term “Tokenization of assets“.
Unlock Your Business Potential with Certified Blockchain Consulting!
Dive into the future of technology with our team of certified blockchain experts. Simply pick the service you need:
Personalized Advice – tailored to your business needs.
Comprehensive Training – for you and your team.
Development Services – innovative solutions from the whitepaper to the finished blockchain.
Programming – with capabilities and tools to succeed.
TALK TO THE EXPERTS TODAYAdvantages & Disadvantages of Tokenization
Remember what is tokenization? Yes, it’s turning sensitive data, like credit card numbers, into a secret code. Only people with special knowledge can turn the code back into the original data. As always, there are advantages and disadvantages.
Advantages
- Safety: It’s like hiding your valuables in a safe. If someone breaks into your house (or computer system), they can’t use the secret code to buy stuff or harm you.
- Flexibility: Businesses can use these secret codes in different systems without exposing the real sensitive data.
- Compliance: Many laws require businesses to protect customer information. This technology helps them do this.
Disadvantages
- Complexity: Setting up tokenization can be complicated. It’s like setting up a new security system for your house.
- Cost: It might cost money to set up and maintain. Think of it like paying for a high-quality lock.
- Dependency: If the system that knows how to decode the secret code has a problem, you might be temporarily locked out from your own information.
Tokenization vs. Encryption: What’s the Difference?

What is tokenization was clearly explained. But there is another thing called Encryption. Both methods keep sensitive information safe. Imagine you have a secret message, and you don’t want others to read it. Here’s how each method works:
Encryption
- This is like changing your secret message using a special code.
- The message is scrambled into a mix of characters that don’t make sense.
- To read the scrambled message, you need a key to decode it. Without the key, it’s nearly impossible to figure out the original message.
In summary: Tokenization swaps out your information for a fake one, while Encryption scrambles your information into a code. Both help keep your secrets safe!
Steps Involved in the Tokenization Process
To understand what is tokenization, we also have to talk about the steps involved. Imagine you have a toy box and you want to organize all your toys inside. It’s like breaking down a big toy (like a puzzle) into smaller pieces and placing each piece in its own tiny box.
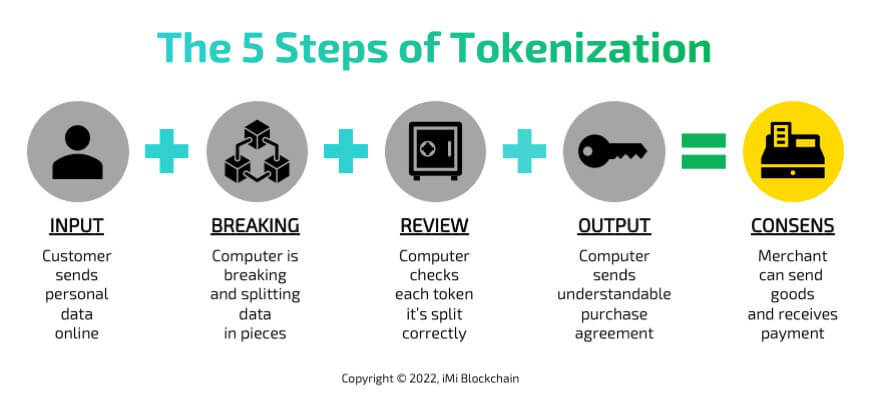
Share this Image on Your Site:
So, if you have a sentence like “I love ice cream,” tokenization will break it down into individual words: “I”, “love”, “ice”, and “cream”. Here are the steps involved:
- Input: Start with the text you want to break down (e.g., “I love ice cream”).
- Breaking: Split the text into smaller parts (tokens).
- Review: Check each token to ensure it’s split correctly.
- Output: Store or use these tokens for whatever task you need, like searching or understanding the text.
Think of it like cutting up a sentence into its words, so a computer can understand and work with each word separately!
Challenges and Considerations when Implementing Tokenization
Let’s break it down. Turning information into a secret code, that’s what is tokenization. This helps keep it safe when you shop online or use an app. However, there are challenges when making or using this secret code. Here are some of them:
- Making the Secret Code: To create the secret code (or “token”), there needs to be a system that can quickly change the information back and forth without mistakes.
- Keeping It Safe: Just like any other valuable thing, tokens can be stolen too. Companies need to keep these tokens safe from hackers.
- Different Systems: Imagine you have a secret code for a game, but then you try to use it in a different game and it doesn’t work. The same thing can happen with tokenization. Different companies might use different secret codes, and they might not work well together.
- Changing the Rules: Sometimes, the rules for how to make or use the secret codes change. This can make it hard for companies to keep up.
- Trust: People and companies need to trust that this secret code system works well and is safe. If they don’t, they might not use it.
So, while turning information into a secret code is a great idea, there are things to think about to make sure it works well for everyone!
Future Trends and Advancements in Tokenization Technology

Now, here are some future trends in tokenization:
- More Digital Items: Just like toys, more things like art, music, and even pieces of property can be represented as tokens. This means you can own a part of a famous painting or song using tokens.
- Better Security: Tokenization can keep important information safe. For instance, when you shop online, your credit card details can be turned into a token. This way, even if hackers try to steal it, they just get the token, not the real card details.
- Playing and Earning: In video games, players might earn tokens for their achievements. Later, they might exchange these for real-world goods or money.
- Easier Trading: People can easily trade tokens, just like trading cards. This makes buying and selling things like digital art or music simpler.
- Greener Technology: Some new token systems are trying to use less energy. This means they’ll be better for the planet.
In short, the future looks exciting! It will change the way we own, trade, and protect things in the digital world.
Key Takeaways
The world is changing super fast. People made technology to help us in our daily lives. We can see this in how we keep our data safe, especially when we pay for stuff using cards. Tokenization-based payment systems, such as Apple Pay, have become increasingly popular for secure online and mobile shopping. The use of tokens, like subway tokens, in these payment systems ensures the security of our transactions and protects our sensitive information, such as payment card data. Tokenization has become widespread as companies continue to create and store tokens in a similar manner.
Like all big ideas, tokenization has good and bad sides. This article talks about some of these, but not all. Even though it’s awesome, it’s important to know it’s not perfect. If you want to learn more, come chat with one of our experts! We hope we explained “what is tokenization” in an easy way for you. If you have questions, then write a comment below.
Learn Crypto!
Book a Crypto Training
Watch our Webinars
Enroll in Crypto Online Courses
Become a Pro yourself
Get Free Crypto Tips!
Get crypto tips.
On top, you’ll get our free blockchain beginners course right away to learn how this technology will change our lives.


